By Yogi Schulz
Here’s the link to my IT blog at IT World Canada
Are you surprised that major oil and natural gas producers investing heavily in cybersecurity defences are nonetheless victims of data breaches and ransomware attacks? Consider this recent headline: Petro-Canada payments systems largely restored in the wake of a cyberattack: Suncor. Are we giving these producers more credit than they deserve, or is it impossible to defend against every attack?
The reality is that it is impossible to thwart every attack. However, minimizing the scope and consequences of successful intrusions is possible with cybersecurity resilience. Cybersecurity resilience refers to an oil and natural gas producer’s ability to withstand and recover from cyber threats, incidents, or disruptions. It encompasses a comprehensive set of practices, strategies, and technologies designed to:
- Protect networks, information systems and data comprehensively.
- Detect and respond to cybersecurity incidents quickly.
- Minimize the impact of data breaches and ransomware attacks.
- Maintain compliance with a growing list of cybersecurity-related regulations.
This article explores the critical elements of cybersecurity resilience and their importance in safeguarding oil and natural gas producers against cyber threats as these increase in frequency and sophistication.
Risk assessment and management
Unfortunately, many oil and natural gas producers do not understand their cybersecurity risks.
Effective cybersecurity resilience begins with thoroughly understanding a producer’s assets, vulnerabilities, and potential threats. Regular risk assessments enable producers to:
- Identify and prioritize their most critical assets.
- Assess the likelihood and impact of potential cyber threats against those critical assets.
- Develop strategies to mitigate and manage those risks.
- Measure continuous improvement or degradation over time.
For a description of what a low-effort but comprehensive risk assessment entails, please watch this video: Assess your SMB cybersecurity defences at warp-speed.
Access controls
Phishing, stealing, and systematically guessing userids and passwords are the most common ways hackers maliciously access networks and applications.
Restrict access to sensitive systems and data based on the principle of least privilege. This principle enables producers to reduce the attack surface and mitigate the impact of potential breaches. Robust authentication mechanisms, such as multi-factor authentication (MFA), further enhance access controls and protect against unauthorized access.
Incident response planning
Without a plan, cybersecurity incident response looks a lot like the Keystone Cops in action.
Incident response planning involves developing a structured approach to respond to and mitigate cybersecurity incidents. This plan includes the following:
- Defining roles and responsibilities.
- Establishing communication channels.
- Documenting response procedures.
Test the plan from time to time through a tabletop exercise. Improve the plan based on findings from the exercise.
A well-defined incident response plan enables producers to swiftly detect and respond to security incidents. A rapid response minimizes incident impacts and reduces the recovery elapsed time.
Data backup and recovery
Without data backup and recovery, producers risk their data that has emerged as a critical asset.
Regular backups of critical data are crucial for cybersecurity resilience. Store backups securely. Regularly test the restoration process to validate backup data integrity.
The ability to restore data from backups to minimize data loss and system outages during a security incident or system failure adds to resiliency.
Continuous monitoring and threat intelligence
Without continuous monitoring, producers have no data about the effectiveness of their cybersecurity defenses.
To effectively defend against cyber threats, producers continuously monitor their networks, computing infrastructure, and applications for potential security breaches. Implementing robust monitoring tools and techniques, such as intrusion detection systems and security information and event management (SIEM) solutions, enables producers to quickly identify and respond to threats.
Integrating threat intelligence feeds, typically from cybersecurity vendors, and staying updated on emerging threats enhances the producer’s ability to proactively detect intrusions and mitigate potential risks.
Network segmentation
Operating a single or flat network is the simplest but far less secure.
Implement network segmentation, using bridges and routers to divide a network into smaller, isolated segments. The significant benefits include the ability to:
- Limit everyone’s access to only the applications they are authorized to access.
- Limit the spread of potential security incidents.
- Simplify isolating incidents and quickly identifying threats.
- Limit third-party access.
- Improve performance and decrease congestion.
- Minimize the impact of network component failures.
Best practices for secure and resilient network operation include:
- Audit and monitor your network to identify subnetwork gaps that intruders can exploit.
- Configure legitimate paths to access resources easier than illegitimate paths.
- Don’t over-segment because it adds unnecessary complexity and makes it more challenging to manage the network.
- Visualize your network to understand traffic better and anticipate issues.
- Combine similar network resources.
Security awareness and training
Simple human errors, negligence and occasional malicious actions significantly contribute to cybersecurity incidents.
Producers must invest in comprehensive security awareness and training programs to educate employees about common threats, phishing attacks, social engineering techniques, and best practices for safe online behaviour. Producers can empower employees to become a resilient line of defence against cyber threats by promoting a security-conscious culture.
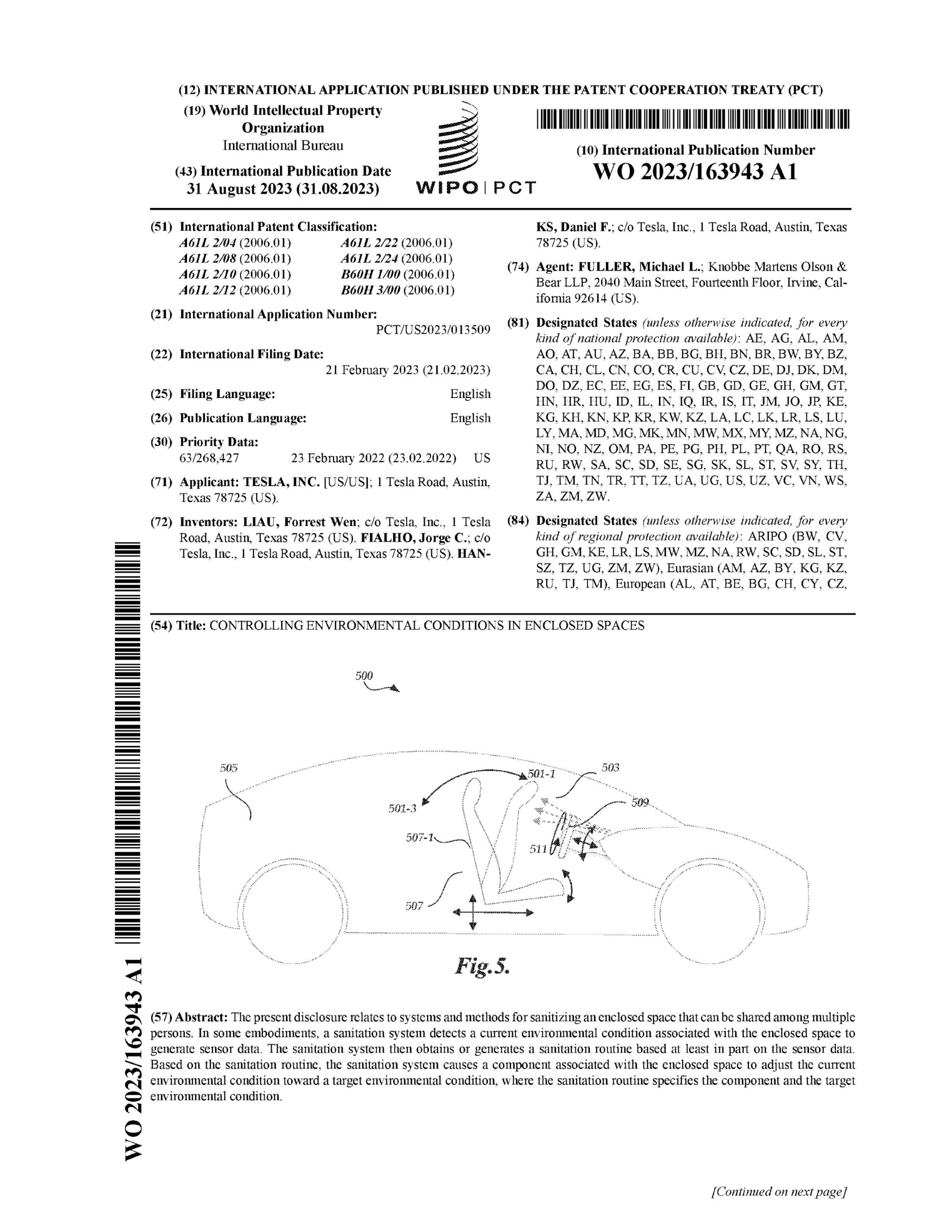
Vendor and supply chain security
Almost all producers rely on third-party vendors for various products and services. These vendors are a cybersecurity risk, especially when using electronic data exchange.
Ensuring the security of these external partners is crucial for overall cybersecurity resilience. Producers should conduct due diligence to assess the security posture of vendors, establish contractual obligations for security requirements, and regularly monitor their compliance.
Security policies and procedures
Vague or non-existent cybersecurity policies cause inadequate responses to inevitable incidents.
Clear and well-defined security policies and procedures lay the foundation for a resilient cybersecurity posture. These policies should describe the following topics:
- Access controls that define multiple roles for networks, systems and data.
- Data classification for multiple restriction levels.
- Incident response procedure.
- Employee awareness training content and frequency.
- Secure software development practices.
Producers promote a security-aware culture and improve adherence to cybersecurity policies by establishing guidelines and best practices.
Regular security testing and auditing
Conducting regular security assessments, penetration testing, and vulnerability scanning identify weaknesses and gaps in a producer’s defences. These proactive measures enable producers to remediate vulnerabilities before malicious actors exploit them. Additionally, regular security audits help ensure compliance with relevant industry standards and regulations.
Incident review and lessons learned
After experiencing a security incident, producers should conduct a thorough post-incident analysis to understand the root causes, the effectiveness of response measures, and areas for improvement. Incorporating lessons learned from previous incidents strengthens a producer’s resilience and helps prevent similar incidents in the future.
In conclusion, cybersecurity resilience requires a holistic approach that combines risk assessment, robust security policies, effective incident response planning, continuous monitoring, access controls, data backup, and recovery, network segmentation, security awareness, and vendor management. By incorporating these key elements, producers can enhance their ability to withstand cyber threats, minimize the impact of incidents, and quickly recover from potential breaches.
Share This: